expand for answer
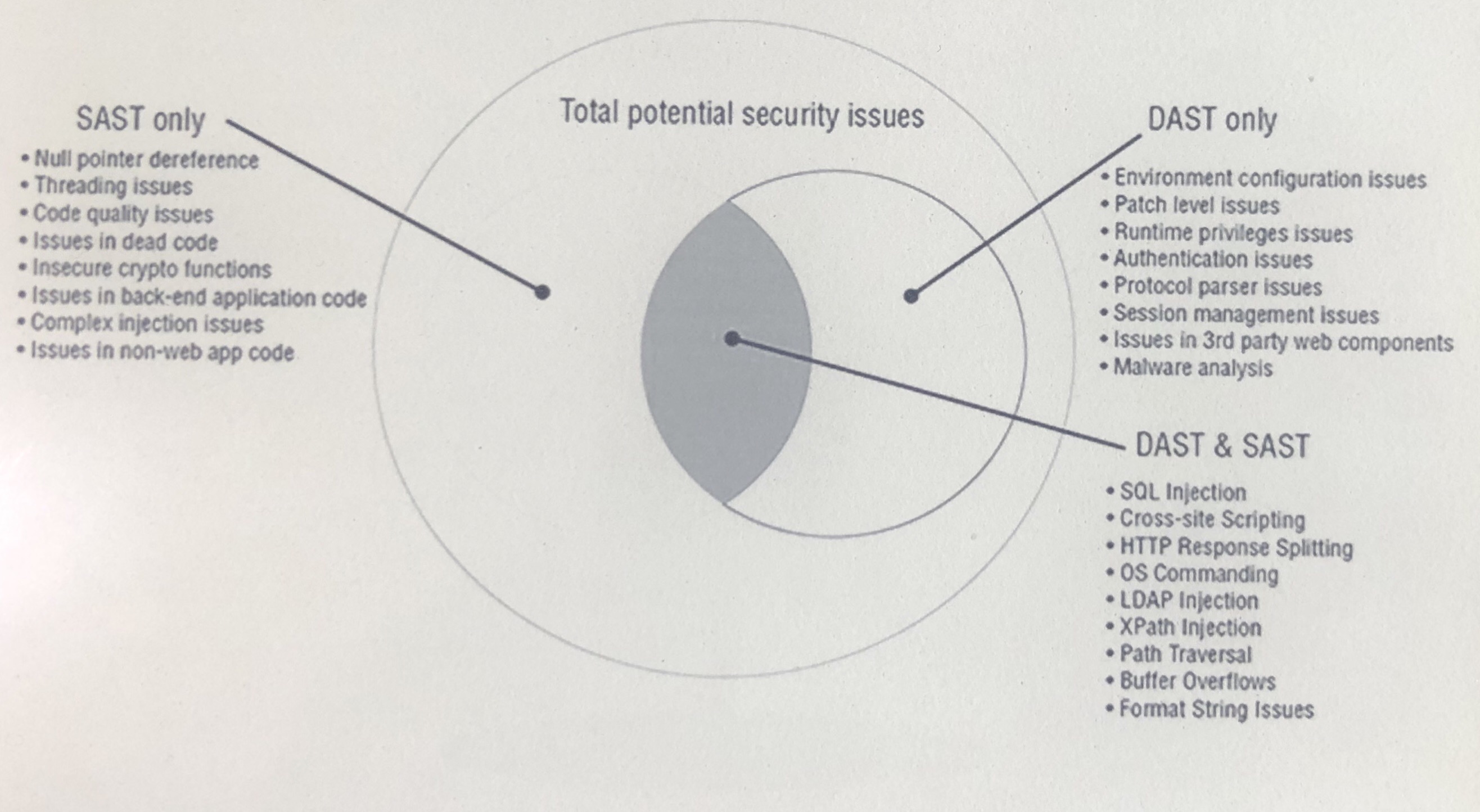
SAST vs DAST Testing Coverage
SAST Only:
- Null pointer dereference
- Threading issues
- Code quality issues
- Issues in dead code
- Insecure crypto functions
- Issues in back-end application code
- Complex injection issues
- Issues in non-web app code
DAST Only:
- Environment configuration issues
- Patch level issues
- Runtime privileges issues
- Authentication issues
- Protocol Parser Issues
- Session management Issues
- Issues in 3rd party web components
- Malware analysis
DAST AND SAST:
- SQL injections
- Cross-site scripting
- HTTP Response Splitting
- OS Commanding
- LDAP injection
- XPATH injection
- Path traversal
- Buffer overflows
- Format String Issues
Similar items:
The address of a record (or other data grouping) contained in another record so that a program may access the former record when it has retrieved the latter record. The address can be absolute, relative, or symbolic, and hence the pointer is referred to as absolute, relative, or symbolic.
[view]
[view]
A protocol used to assign TCP/IP configuration settings to systems upon bootup. DHCP uses UDP port 67 for server point- to-point response and port 68 for client request broadcast. DHCP supports centralized control and management of network addressing. DHCP is an industry standard protocol used to dynamically assign IP addresses to network devices.
[view]
[view]
The collection of standards, specifications, and guidelines, architecture definitions, software infrastructures, reusable components, application programming interfaces (APIs), methodology, runtime environment definitions, reference implementations, and methodology, that establishes an environment on which a system can be built. The COE is the vehicle that assures interoperability through a reference implementation that provides identical implementation of common functions. It is important to realize that the COE is both a standard and an actual product.
[view]
[view]
A security technique that provides a security boundary for applications and prevents the application from interacting with other applications. Anti-malware applications use sandboxing techniques to test unknown applications. If the application displays suspicious characteristics, the sandboxing technique prevents the application from infecting other applications or the operating system.
[view]
[view]
The individual or organization responsible for configuration control or configuration management.
[view]
[view]
There are no comments yet.